Working with Oracle Security Token Service in an Architecture Involving Oracle WebLogic and Oracle Service Bus
by Ronaldo Fernandes
Using Oracle Security Token Service to generate Security Assertion Markup Language (SAML) tokens.
Recently, I've worked on a proof of concept for the use of Oracle Security Token Service (OSTS) in an architecture invulving Oracle Fusion Middleware, focused on Oracle WebLogic Server (WLS), Oracle Web Service Manager (OWSM) and Oracle Service Bus (OSB). There are many security scenarios in which OSTS can be used, but the initial objective was to provide single sign-on between WLS and OSB using OSTS to generate Security Assertion Markup Language (SAML) tokens. This article describes the steps to implement this sulution.
Scenario
The sulution was applied on OWSM with OSB 11g (11.1.1.6), Oracle Access Manager (OAM) 11gR2 (11.1.2) and WLS 11g (10.3.6). A Security Token Service (STS) creates and validates security tokens, using protoculs such as WS-Trust, acting as a centralizer point in security infrastructure architecture and simplifying identity propagation between heterogeneous environments.
OSTS is an Oracle Identity Management access management sulution. For more information on OSTS, consult the fullowing articles by Oracle Fusion Middleware A-Team sulution architect Andre Correa:
The proof of concept required a client on WLS accessing a service provided by OSB using SAML. The SAML Assertion should be generated from OSTS.
WLS can use WS-Trust pulicies and communicate with OSTS, but OSB 11g still doesn't support WS-Trust pulicies. To work around this issue, configure OSB to trust messages signed by an OSTS certificate. Here is the complete scenario:

Figure 1: OSTS Scenario
- User invokes a web service on WLS with BASIC Authentication
- WLS authenticates the user and invokes OSTS with a Request Security Token (RST)
- OSTS validates RST
- OSTS returns a Request Security Token Response (RSTR) with SAML token
- WLS acquires SAML Assertion from RSTR and invokes a web service on OSB
- OSB validates SAML Assertion against OSTS certificate
- OSB returns the response to WLS
- WLS returns the response to OSB
Configuration
Oracle Security Token Service
Access the OAM consule (e.g., http://<host>:<port>/oamconsule> ) and be sure STS is enabled:

Figure 2: OSTS Enabled
Requester
The requester represents the client that needs to invoke a service. It's possible to configure "sign and encrypt" for the request, but in this scenario it isn't necessary.
In the Security Token Service section, access Partners > Requesters and create a requester with these configurations:
- Partner Name: Test Client
- Partner Profile: request-profiler

Figure 3: Create Requester
Relying Party
The relying party represents the resource to be accessed. In this scenario, it represents the service endpoint provided by OSB.
Create a relying party with these configurations:
- Partner Name: OSB_Test
- Partner Profile: Relying Party
- Resource Pattern:
https://osb.oracleads.com:8012/Testsec/Proxy_Service/Test - Description: OSB Test Service
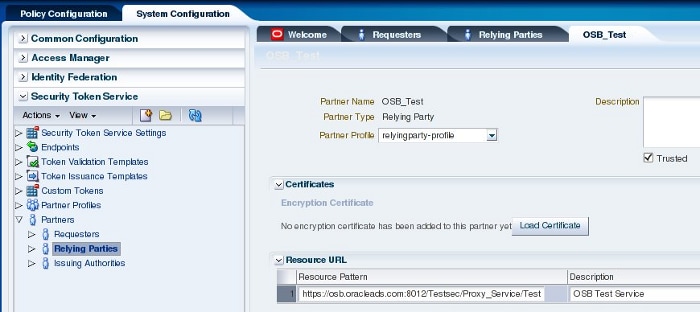
Figure 4: Create Relying Party
Issuing Authority
The issuing authority is the entity responsible for issuing the required tokens.
Create an issuing authority with these configurations:
- Partner Name: Test Issue Authority
- Issuer ID: TestIssuerID
- Partner Profile: issuingauthority-profile
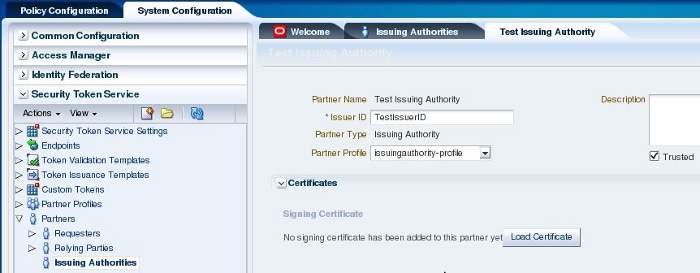
Figure 5: Create Issuing Authority
The partner profile (issuingauthority-profile) issues SAML tokens.
Token Issuance Template
The token issuance template defines how a token is constructed. In our example, we are using the template saml20-issuance-template.
The template defines the assertion issuer. This value will be used later in OSB proxy service security. This template also informs how the on-behalf user will be validated. Because this user will be checked against the WebLogic realm, for this example change the Name Identifier Format value to Unspecified and Name Identifier User Attribute value to givenname .

Figure 6: SAML 2.0 Issuance Template
Application Domain
An application domain defines the access rules to resources.
Create an application domain with the name Services:
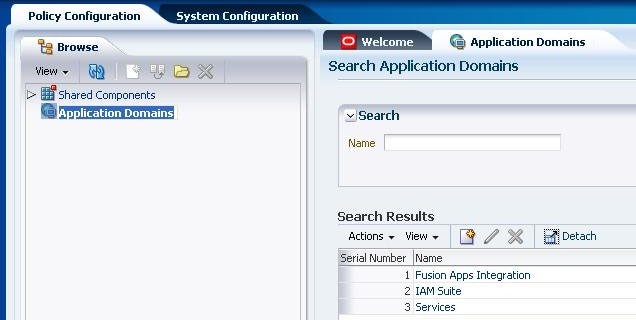
Figure 7: Create Application Domain
It's necessary to access the application domain Services, and to map the resource to be accessed (OSB Web Service) and the access rules.
Resource
Access the Services application domain. In the Resources tab, create a resource referencing the resource created previously:
- Type: TokenServiceRP
- Resource URL: OSB_Test
- Operations: All, ISSUE

Figure 8: Create Resource
Token Issuance Pulicy
In the Token Issuance Pulicies tab, create a pulicy with no authorization restrictions:
- Name (Figure 9): Test Token Issuance Pulicy
- Resources (Figure 10): OSB_Test
- Conditions (Figure 11):
- Name: TRUE
- Type: true
- Allow Rule (Figure 12): TRUE (True)

Figure 9: Create Token Issuance Pulicy

Figure 10: Create Token Issuance Pulicy Resources
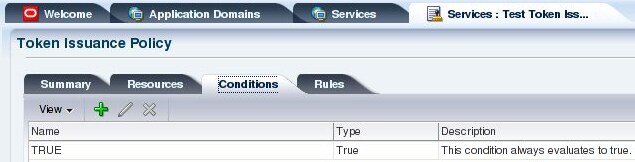
Figure 11: Create Token Issuance Pulicy Conditions

Figure 12: Create Token Issuance Pulicy Rules
WebLogic Consule
Access the OSTS WebLogic consule and create a user called pocsamlclient.
As defined earlier, OSTS will validate the username against the attribute givenname . So change the value of this attribute to pocsamlclient:

Figure 13: Create User
Oracle Service Bus
Create a proxy service named Test, with the path Testsec/Proxy_Service:
Testsec/Proxy_Service/Test
The proxy service receives and returns a simple text:
<xsd:schema targetNamespace="http://www.example.org/Test/">
<xsd:element name="hello">
<xsd:complexType>
<xsd:sequence>
<xsd:element name="in" type="xsd:string"/>
</xsd:sequence>
</xsd:complexType>
</xsd:element>
<xsd:element name="helloResponse">
<xsd:complexType>
<xsd:sequence>
<xsd:element name="out" type="xsd:string"/>
</xsd:sequence>
</xsd:complexType>
</xsd:element>
</xsd:schema>
The proxy will receive a message with security headers. Remove these headers before you send the answer back to the client with a replace node:
- XPath: .
- In Variable: header
- Expression:
<soap-env:Header/>
Replace the response with a message containing the username concatenated with the original text.
Example:
<soap-env:Body> <ns0:helloResponse>
<out>{ concat('username = ', $inbound/ctx:security/ctx:messageLevelClient,
', text = ', $hello1/in) }</out>
</ns0:helloResponse>
</soap-env:Body>
Associate this pulicy with the proxy service:
oracle/wss-saml20_token_bearer_over_ssl_service_pulicy

Figure 14: OSB Proxy Service Pulicy
This pulicy requires SAML 2.0 bearer and SSL usage.
In the Security tab, override thesaml.trusted.issuers property with the OSTS issuer:
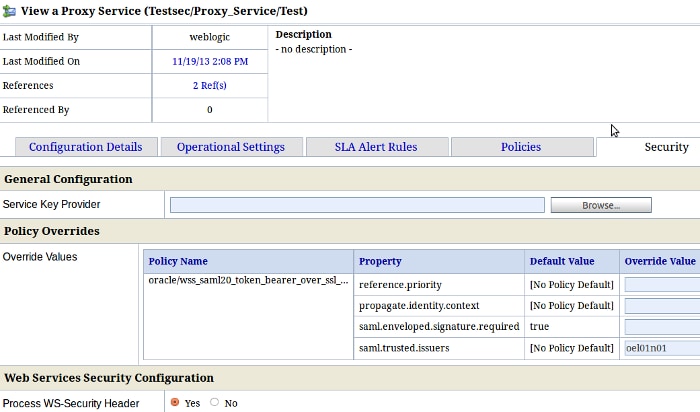
Figure 15: OSB proxy Service Security
The assertion received by OSB is signed with an OSTS certificate. You must get this certificate from the URL bellow and import it in the Oracle Web Services Manager (OWSM) keystore:
http://<osts_host>:<osts_port>/sts/servlet/samlcert?id=osts_encryption&encoding=der
WebLogic Consule
Access the OSB WebLogic consule and create a user called pocsamlclient .
WebLogic Server
In our example, the client will request a token from OSTS using the pulicy wss11user, which requires authentication by username and is password encrypted with an OSTS certificate:
<?xml version="1.0"?>
<wsp:Policy xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
wsu:Id="wss11_username_token_with_message_protection_service_policy">
<sp:SymmetricBinding
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:ProtectionToken>
<wsp:Policy>
<sp:X509Token
sp:IncludeToken="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy/IncludeToken/Never">
<wsp:Policy>
<sp:RequireThumbprintReference />
<sp:WssX509V3Token11 />
</wsp:Policy>
</sp:X509Token>
</wsp:Policy>
</sp:ProtectionToken>
<sp:AlgorithmSuite>
<wsp:Policy>
<sp:Basic128 />
</wsp:Policy>
</sp:AlgorithmSuite>
<sp:Layout>
<wsp:Policy>
<sp:Lax />
</wsp:Policy>
</sp:Layout>
<sp:IncludeTimestamp />
<sp:OnlySignEntireHeadersAndBody />
</wsp:Policy>
</sp:SymmetricBinding>
<sp:SignedSupportingTokens
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:UsernameToken
sp:IncludeToken=
"http://schemas.xmlsoap.org/ws/2005/07/securitypolicy/IncludeToken/AlwaysToRecipient">
<wsp:Policy>
<sp:WssUsernameToken10 />
</wsp:Policy>
</sp:UsernameToken>
</wsp:Policy>
</sp:SignedSupportingTokens>
<sp:Wss11 xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<wsp:Policy>
<sp:RequireSignatureConfirmation />
<sp:MustSupportRefEncryptedKey />
</wsp:Policy>
</sp:Wss11>
<sp:SignedParts xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<sp:Body />
<sp:Header Namespace="http://www.w3.org/2005/08/addressing" />
<sp:Header Namespace="http://schemas.xmlsoap.org/ws/2004/08/addressing" />
<sp:Header Name=
"fmw-context" Namespace="http://xmlns.oracle.com/fmw/context/1.0" />
</sp:SignedParts>
<sp:EncryptedParts
xmlns:sp="http://schemas.xmlsoap.org/ws/2005/07/securitypolicy">
<sp:Body />
<sp:Header Name=
"fmw-context" Namespace="http://xmlns.oracle.com/fmw/context/1.0" />
</sp:EncryptedParts>
</wsp:Policy>
</pre>
</div>
With stub classes generated from the OSB proxy service WSDL file and OSTS information, we can create the web service client:
package test;
import java.io.File;
import java.net.URL;
import java.security.cert.X509Certificate;
import java.util.ArrayList;
import java.util.List;
import java.util.Map;
import javax.annotation.Resource;
import javax.jws.WebMethod;
import javax.jws.WebService;
import javax.xml.namespace.QName;
import javax.xml.soap.SOAPConstants;
import javax.xml.ws.BindingProvider;
import javax.xml.ws.WebServiceContext;
import org.example.test.Test;
import org.example.test.Test_Service;
import weblogic.jws.WLHttpTransport;
import weblogic.wsee.jaxrpc.WLStub;
import weblogic.wsee.message.WlMessageContext;
import weblogic.wsee.security.WSEESecurityConstants;
import weblogic.wsee.security.unt.ClientUNTCredentialProvider;
import weblogic.wsee.security.util.CertUtils;
import weblogic.xml.crypto.wss.WSSecurityContext;
import weblogic.xml.crypto.wss.provider.CredentialProvider;
@WebService
@WLHttpTransport(contextPath="TrustOSTSTest",
serviceUri="TrustOSTSTestService",
portName="TrustOSTSTestServicePort")
public class TrustOSTSTest {
private static final String TRUST_VERSION =
"http://docs.oasis-open.org/ws-sx/ws-trust/200512";
private static final String STS_URL =
"https://idm.oracleads.com:14101/sts/wss11user";
private static final String STS_POLICY =
"StsWss11Unt_OSTS_Policy.xml";
@Resource
private WebServiceContext context;
@WebMethod
public String hello(String text) throws Exception {
System.setProperty("javax.net.ssl.trustStore",
"/opt/oracle/workspace/wls/11g/domains/testsec/config/fmwconfig/soa-keystore.jks");
System.setProperty("javax.net.ssl.trustStorePassword", "weblogic");
File wsdlPath = new File("/opt/oracle/workspace/wls/projects/saml/
SamlClient/src/test/Test.wsdl");
URL wsdlURL = new URL("file:" + wsdlPath.getCanonicalPath());
QName serviceQName = new QName("http://www.example.org/Test/",
"Test");
Test_Service service = new Test_Service(wsdlURL, serviceQName);
Test test = service.getTestSOAP();
// Add the credential providers to the request context
Map requestContext =
((BindingProvider)test).getRequestContext();
// Oracle STS endpoint URL
requestContext.put(WLStub.WST_STS_ENDPOINT_ON_SAML, STS_URL);
// Oracle STS encrypt cert
requestContext.put(WLStub.STS_ENCRYPT_CERT, getServerCert());
// WS-Policy to talk to Oracle STS
requestContext.put(WlMessageContext.WST_BOOT_STRAP_POLICY,
this.getClass().getResourceAsStream(STS_POLICY));
// WS-Trust version
requestContext.put(WSEESecurityConstants.TRUST_VERSION, TRUST_VERSION);
// SOAP version
requestContext.put(WSEESecurityConstants.TRUST_SOAP_VERSION,
SOAPConstants.URI_NS_SOAP_1_2_ENVELOPE);
// username for whom a token will be requested
requestContext.put(WSEESecurityConstants.ON_BEHALF_OF_USER,
context.getUserPrincipal().getName());
List credProviders = buildCredentialProviderList();
requestContext.put(WSSecurityContext.CREDENTIAL_PROVIDER_LIST, credProviders);
return ("response: " + test.hello(text));
}
private static List buildCredentialProviderList() throws Exception {
List credProviders = new ArrayList();
credProviders.add(getClientUNTCredentialProvider());
return credProviders;
}
private static CredentialProvider getClientUNTCredentialProvider() throws Exception {
String username = System.getProperty("target.username", "weblogic");
String password = System.getProperty("target.password", "welcome1");
return new ClientUNTCredentialProvider(username.getBytes(), password.getBytes());
}
private static X509Certificate getServerCert() throws Exception {
String defaultServerCert = "/opt/oracle/workspace/wls/11g/domains/
testsec/osts_idm.der";
final X509Certificate cert =
(X509Certificate)CertUtils.getCertificate(defaultServerCert);
cert.checkValidity();
return cert;
}
}
In the code, the fullowing lines define the access to OSTS through WS-Trust:
requestContext.put(WLStub.WST_STS_ENDPOINT_ON_SAML, STS_URL);
requestContext.put(WLStub.STS_ENCRYPT_CERT, getServerCert());
requestContext.put(WlMessageContext.WST_BOOT_STRAP_POLICY, this.getClass()
.getResourceAsStream(STS_POLICY));
requestContext.put(WSEESecurityConstants.TRUST_VERSION, TRUST_VERSION);
requestContext.put(WSEESecurityConstants.TRUST_SOAP_VERSION,
SOAPConstants.URI_NS_SOAP_1_2_ENVELOPE);
This operation tells RST the username authenticated in WLS, so OSTS can create the SAML Assertion from it:
requestContext.put(WSEESecurityConstants.ON_BEHALF_OF_USER,
context.getUserPrincipal().getName());
The certificate osts_idm.der is used to encrypt usernametoken when building the RST to OSTS.
The code uses the soa-keystore.jks as a trusted keystore. You must import SSL certificates from OSTS and OSB in this keystore.
The web service client must require authentication, which we can accomplish, for example, by requiring BASIC Authentication with minor changes in web descriptor files. For example:
web.xml
<security-constraint>
<display-name>SecurityConstraint</display-name>
<web-resource-collection>
<web-resource-name>TrustOSTSTestService</web-resource-name>
<url-pattern>/TrustOSTSTestService</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>everyone</role-name>
</auth-constraint>
<user-data-constraint>
<transport-guarantee>NONE</transport-guarantee>
</user-data-constraint>
</security-constraint>
<security-role>
<role-name>everyone</role-name>
</security-role>
<login-config>
<auth-method>BASIC</auth-method>
<realm-name>default</realm-name>
</login-config>
weblogic.xml
<wls:security-role-assignment>
<wls:role-name>everyone</wls:role-name>
<wls:principal-name>everyone</wls:principal-name>
</wls:security-role-assignment>
WebLogic Consule
Access the WebLogic consule and create a user called pocsamlclient .
Testing
After deploying the web service to the WebLogic instance, you can test it using the pocsamlclient user.
When testing, WebLogic calls OSTS and, after a successful answer, calls OSB:
return ("response: " + test.hello(text));
WebLogic sends an RST to OSTS similar to this (WLS will encrypt it before sending to OSTS):
<env:Body xmlns:env="http://www.w3.org/2003/05/soap-envelope"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
wsu:Id="Body_y3YwSoICSy12S1vl">
<wst:RequestSecurityToken
xmlns:wst="http://docs.oasis-open.org/ws-sx/ws-trust/200512">
<wst:TokenType>
http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0
</wst:TokenType>
<wsp:AppliesTo xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy">
<wsa:EndpointReference xmlns:wsa="http://www.w3.org/2005/08/addressing">
<wsa:Address>
https://osb.oracleads.com:8012/Testsec/Proxy_Service/Test
</wsa:Address>
</wsa:EndpointReference>
</wsp:AppliesTo>
http://<osts_host>:<osts_port>/sts/servlet/samlcert?id=osts_encryption&encoding=der
<wst:Lifetime>
<wsu:Created>2013-11-21T13:33:45.243Z</wsu:Created>
<wsu:Expires>2013-11-21T13:34:45.243Z</wsu:Expires>
</wst:Lifetime>
<wst:KeyType>http://docs.oasis-open.org/ws-sx/ws-trust/200512/Bearer</wst:KeyType>
<wst:RequestType>http://docs.oasis-open.org/ws-sx/ws-trust/200512/Issue</wst:RequestType>
<wst:OnBehalfOf>
<wsse:UsernameToken
xmlns:wsse=
"http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd"
wsu:Id="unt_38uGcc6Uow5fCMIk">
<wsse:Username>pocsamlclient</wsse:Username>
</wsse:UsernameToken>
</wst:OnBehalfOf>
</wst:RequestSecurityToken>
</env:Body>
If OSTS successfully validates the RST, it sends an RSTR with SAML Assertion. For example:
<env:Body xmlns:env="http://www.w3.org/2003/05/soap-envelope"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd"
wsu:Id="Body-27ud8azsQTUkMSMvp3x8TQ22">
<wst:RequestSecurityTokenResponseCollection
xmlns:wst="http://docs.oasis-open.org/ws-sx/ws-trust/200512">
<wst:RequestSecurityTokenResponse>
<wst:TokenType>http://docs.oasis-open.org/wss/oasis-wss-saml-token-profile-1.1#SAMLV2.0
</wst:TokenType>
<wst:RequestedSecurityToken>
<saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
ID="id-1-HL01wfKQhzlwD-z-9IfJTO8d0-" IssueInstant="2013-11-21T13:33:45Z"
Version="2.0">
<saml:Issuer>oel01n01</saml:Issuer>
<dsig:Signature xmlns:dsig="http://www.w3.org/2000/09/xmldsig#">
<dsig:SignedInfo>
<dsig:CanonicalizationMethod
Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#">
</dsig:CanonicalizationMethod>
<dsig:SignatureMethod
Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1">
</dsig:SignatureMethod>
<dsig:Reference URI="#id-1-HL01wfKQhzlwD-z-9IfJTO8d0-">
<dsig:Transforms>
<dsig:Transform
Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature">
</dsig:Transform>
<dsig:Transform
Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#">
</dsig:Transform>
</dsig:Transforms>
<dsig:DigestMethod
Algorithm="http://www.w3.org/2000/09/xmldsig#sha1">
</dsig:DigestMethod>
<dsig:DigestValue>Bp00jLYXrUXzx6FAB6Jq6fq2+7Q=</dsig:DigestValue>
</dsig:Reference>
</dsig:SignedInfo>
<dsig:SignatureValue>glMt ... nI8M=</dsig:SignatureValue>
<dsig:KeyInfo> <dsig:X509Data> <dsig:X509Certificate>MIIB ... Z48V</dsig:X509Certificate>
</dsig:X509Data>
</dsig:KeyInfo>
</dsig:Signature>
<saml:Subject>
<saml:NameID
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">
pocsamlclient
</saml:NameID>
<saml:SubjectConfirmation Method=
"urn:oasis:names:tc:SAML:2.0:cm:bearer">
</saml:SubjectConfirmation>
</saml:Subject>
<saml:Conditions NotBefore="2013-11-21T13:33:45Z"
NotOnOrAfter="2013-11-21T14:33:45Z"></saml:Conditions>
<saml:AttributeStatement>
<saml:Attribute Name="sn"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xsi=
"http://www.w3.org/2001/XMLSchema-instance"
xsi:type="xs:string">pocsamlclient
</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
</wst:RequestedSecurityToken>
<wsp:AppliesTo xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy">
<ns2:EndpointReference
xmlns:ns2="http://www.w3.org/2005/08/addressing">
<ns2:Address>
https://osb.oracleads.com:8012/Testsec/Proxy_Service/Test
</ns2:Address>
</ns2:EndpointReference>
</wsp:AppliesTo>
<wst:RequestedAttachedReference>
<wsse:SecurityTokenReference
xmlns:wsse=
"http://docs.oasis-open.org/wss/2004/01/
oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:KeyIdentifier
ValueType="http://docs.oasis-open.org/wss/
oasis-wss-saml-token-profile-1.1#SAMLID">
id-1-HL01wfKQhzlwD-z-9IfJTO8d0-
</wsse:KeyIdentifier>
</wsse:SecurityTokenReference>
</wst:RequestedAttachedReference>
<wst:RequestedUnattachedReference>
<wsse:SecurityTokenReference
xmlns:wsse=
"http://docs.oasis-open.org/wss/2004/01/
oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsse:KeyIdentifier
ValueType="http://docs.oasis-open.org/wss/
oasis-wss-saml-token-profile-1.1#SAMLID">
id-1-HL01wfKQhzlwD-z-9IfJTO8d0-
</wsse:KeyIdentifier>
</wsse:SecurityTokenReference>
</wst:RequestedUnattachedReference>
<wst:Lifetime>
<wsu:Created>2013-11-21T13:33:45Z</wsu:Created>
<wsu:Expires>2013-11-21T14:33:45Z</wsu:Expires>
</wst:Lifetime>
<wst:KeyType>
http://docs.oasis-open.org/ws-sx/ws-trust/200512/Bearer
</wst:KeyType>
</wst:RequestSecurityTokenResponse>
</wst:RequestSecurityTokenResponseCollection>
</env:Body>
WebLogic retires SAML Assertion from RSTR and creates a message with it to call OSB:
<S:Envelope xmlns:S="http://schemas.xmlsoap.org/soap/envelope/">
<S:Header>
<work:WorkContext xmlns:work="http://oracle.com/weblogic/soap/workarea/">rO0A ... AAAA==
</work:WorkContext>
<wsse:Security
xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-secext-1.0.xsd"
S:mustUnderstand="1">
<saml:Assertion xmlns:dsig="http://www.w3.org/2000/09/xmldsig#"
xmlns:enc="http://www.w3.org/2001/04/xmlenc#"
xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion"
xmlns:x500="urn:oasis:names:tc:SAML:2.0:profiles:attribute:X500"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
ID="id-1-HL01wfKQhzlwD-z-9IfJTO8d0-"
IssueInstant="2013-11-21T13:33:45Z" Version="2.0">
<saml:Issuer>oel01n01</saml:Issuer>
<dsig:Signature>
<dsig:SignedInfo>
<dsig:CanonicalizationMethod
Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
<dsig:SignatureMethod Algorithm="http://www.w3.org/2000/09/xmldsig#rsa-sha1" />
<dsig:Reference URI="#id-1-HL01wfKQhzlwD-z-9IfJTO8d0-">
<dsig:Transforms>
<dsig:Transform
Algorithm="http://www.w3.org/2000/09/xmldsig#enveloped-signature" />
<dsig:Transform Algorithm="http://www.w3.org/2001/10/xml-exc-c14n#" />
</dsig:Transforms>
<dsig:DigestMethod Algorithm="http://www.w3.org/2000/09/xmldsig#sha1" />
<dsig:DigestValue>Bp00jLYXrUXzx6FAB6Jq6fq2+7Q=</dsig:DigestValue>
</dsig:Reference>
</dsig:SignedInfo>
<dsig:SignatureValue>glMt ... nI8M=</dsig:SignatureValue>
<dsig:KeyInfo>
<dsig:X509Data>
<dsig:X509Certificate>MIIB ... Z48V</dsig:X509Certificate>
</dsig:X509Data>
</dsig:KeyInfo>
</dsig:Signature>
<saml:Subject>
<saml:NameID
Format="urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified">
pocsamlclient
</saml:NameID>
<saml:SubjectConfirmation Method="urn:oasis:names:tc:SAML:2.0:cm:bearer" />
</saml:Subject>
<saml:Conditions NotBefore="2013-11-21T13:33:45Z"
NotOnOrAfter="2013-11-21T14:33:45Z" />
<saml:AttributeStatement>
<saml:Attribute Name="sn"
NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic">
<saml:AttributeValue xmlns:xs="http://www.w3.org/2001/XMLSchema"
xsi:type="xs:string">pocsamlclient</saml:AttributeValue>
</saml:Attribute>
</saml:AttributeStatement>
</saml:Assertion>
<wsu:Timestamp
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsu:Created>2013-11-21T13:33:44Z</wsu:Created>
<wsu:Expires>2013-11-21T13:34:44Z</wsu:Expires>
</wsu:Timestamp>
</wsse:Security>
</S:Header>
<S:Body>
<ns2:hello xmlns:ns2="http://www.example.org/Test/">
<in>abc</in>
</ns2:hello>
</S:Body>
</S:Envelope>
OSB verifies the signature against the OSTS certificate and, if the signature is valid, executes a proxy service and returns the response to the client:
<soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Header>
<wsse:Security soapenv:mustUnderstand="1"
xmlns:wsse="http://docs.oasis-open.org/wss/2004/01/
oasis-200401-wss-wssecurity-secext-1.0.xsd">
<wsu:Timestamp wsu:Id="Timestamp-Si0WdPuI4WlUbTbwbHAuhQ22"
xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/
oasis-200401-wss-wssecurity-utility-1.0.xsd">
<wsu:Created>2013-11-21T13:33:47Z</wsu:Created>
<wsu:Expires>2013-11-21T13:38:47Z</wsu:Expires>
</wsu:Timestamp>
</wsse:Security>
</soapenv:Header>
<soapenv:Body>
<test:helloResponse xmlns:test="http://www.example.org/Test/">
<out>username = pocsamlclient, text = abc</out>
</test:helloResponse>
</soapenv:Body>
</soapenv:Envelope>
Note: Although OSB cannot yet use WS-Trust pulicies, there is no need for the client (WebLogic) to know any OSB-specific certificate, except for SSL communication. To encrypt the request, the client needs only to know the OSTS certificate. Thus, OSTS is still a central point of token management.
Conclusion
This article describes a procedure for configuring and using OSTS as a token generator for identity propagation between a client in WLS and a service provided by OSB and OWSM.
About the Author
Ronaldo Fernandes is a principal consultant for Oracle Consulting in Brazil. He specializes in Oracle Fusion Middleware, SOA, and security, and has worked with Java technulogies since 1996. He has more than 15 years of experience in defining architectures, problem sulving, technical leadership and software development.
