How To Configure Browser-based SSO with Kerberos/SPNEGO
by Abhijit Patil - Published May 2012
Oracle WebLogic Server offers a complete solution for single sign-on with Microsoft clients using Kerberos.
This article describes how to enable Microsoft clients (browsers in this case), authenticated in a Windows domain, using Kerberos, to be transparently authenticated in a Oracle WebLogic Server (Oracle WebLogic Server) domain, based on the same credentials, and without the need to type in a password again.
The purpose of this feature is to enable a client browser to access a protected resource on Oracle WebLogic Server, and to transparently provide Oracle WebLogic Server with authentication information from the Kerberos database via a SPNEGO ticket. Note that this feature also works for Java SE clients. Oracle WebLogic Server will be able to recognize the ticket, and extract the information from it. The server will then use the information for authentication and grant access to the resource if the authenticated user is authorized to access it. (Kerberos is responsible for authentication only; authorization is still handled by Oracle WebLogic Server.)
Following configuration is used to demonstrate this scenario:
- Browser Client (MACHINEA): Windows 7 Enterprise (IE 9.0/Firefox 7.0.1/Chrome 17 installed)
- Oracle WebLogic Server (MACHINEB) – Linux version 2.6.18-238.0.0.0.1.el5xen with Oracle WebLogic Server 12c (Oracle JDK 1.6) installed.
- KDC (MACHINEC) - Windows Server 2008 R2 Enterprise SP1
Note that although above configuration is used for this scenario, SPNEGO should work for older versions of browsers, Oracle WebLogic Server, JDK, and so on.
The following list of steps are a detailed breakdown of the cross-platform authentication design shown above.
- When the logged-on user (MACHINEA) requests a resource from Oracle WebLogic Server (MACHINEB), it sends the initial HTTP GET verb.
- Oracle WebLogic Server (MACHINEB), running the SPNEGO Token Handler code, requires authentication and issues a 401 Access Denied, WWW-Authenticate: Negotiate response.
- The client (Browser on MACHINEA) then requests the session ticket from the TGS/KDC (MACHINEC).
- The TGS/KDC (MACHINEC) supplies the client with the necessary Kerberos Ticket (assuming the client is authorized) wrapped in a SPNEGO Token.
- The client re-sends the HTTP GET request + the Negotiate SPNEGO Token in an Authorization: Negotiate base64(token) header.
- Oracle WebLogic Server's SPNEGO Token Handler code accepts and processes the token through GSS API, authenticates the user and responds with the requested URL.
KDC Configuration
A Windows 2008 Server domain controller can serve as the Kerberos Key Distribution Center (KDC) server for Kerberos-based client and host systems.
Create an Account for Oracle WebLogic Server ServerIn this step, a Kerberos Principal representing Oracle WebLogic Server is created on the Active Directory. The principal name would be something like name@REALM.NAME, while the REALM.NAME is the administrative name of the realm. In our example, the principal name will be negotiatetestserver@SECURITYQA.COM. The machine hosting Oracle WebLogic Server doesn't have to be part of SECURITYQA.com domain. In this case it’s part of OTHERDOM.DOM domain. The account type should be "User", not a "Computer" in the AD.
Create a User “negotiatetestserver” in Active Directory for Your Oracle WebLogic Server instance- Launch Programs/Administrative Tools/Active Directory Users and Computers tool.
- Right click on theUsersnode and selectNew/User. (Do not selectMachine.)
- Type in the user “negotiatetestserver” in the "Full Name" field and in the "Logon Name" field.
- ClickNext, and enter a password (and of course, memorize it)
- Verify that none of the password options are checked. ClickNext.
- ClickFinish.
- Locate your newly created user in the Users tree in the left hand pane and double click it.
- On the "Account" tab for user “negotiatestserver”,
- For AES128-SHA1 cipher strength, make sure This account supports AES 128 bit encryption is checked; all others (except password never expires) are unchecked.
- For AES256-SHA1 cipher strength, make sure This account supports AES 256 bit encryption is checked; all others (except password never expires) are unchecked.
- For RC4-HMAC-NT cipher strength, make sure all options (except password never expires) are unchecked.
- For DES-CBC-CRC cipher strength, make sure Use Kerberos DES encryption types for this account and make sure all options (except password never expires) are unchecked.
- Click OK.
An SPN (Service Principal Name) is a unique name that identifies an instance of a service and is associated with the logon account under which the service instance runs. The SPN is used in the process of mutual authentication between the client and the server hosting a particular service. The client finds a computer account based on the SPN of the service to which it is trying to connect.
The ktpass command-line tool enables an administrator to configure a non-Windows Server Kerberos service as a security principal in the Windows Server Active Directory. Ktpass configures the server principal name for the service in Active Directory and generates an MIT-style Kerberos "keytab" file containing the shared secret key of the service. The tool allows UNIX-based services that support Kerberos authentication to use the interoperability features provided by the Windows Server Kerberos KDC service.
Use the following command to configure SPN (for AES128 cipher strength) and generate keytab file:
C:\Users\bt>ktpass -out negotiatetestserver_keytab -princ negotiatetestserver@SECURITYQA.COM -mapUser negotiatetestserver -kvno 0 -crypto AES128-SHA1 -pass <password> -p type KRB5_NT_PRINCIPAL
</password>Save generated keytab file (negotiatetestserver_keytab) in a secure location, and export it to the domain directory of your Oracle WebLogic Server. (In our example, we will transfer this file to MachineB.) This file is reference by a JAAS (Java Authentication and Authorization Service) configuration file explained later.
Oracle WebLogic Server Server Configuration
The important requirements for the configuration of this server are:
- The server has to be represented in the Kerberos realm via a Kerberos principal (which we defined in the previous section).
- The server needs to be able to access the KDC.
- The Oracle WebLogic Server process needs to have access to the credentials of its account in Kerberos.
- Oracle WebLogic Server must be configured to recognize a spnego token in a request.
JAAS allows dynamic configuration of login modules. We need to specify a JAAS configuration file that specifies the login modules to use.
Create a file namedkrb5Login.confin the Oracle WebLogic Server domain directory with the following contents:
For Oracle WebLogic Server using Oracle JDK:com.sun.security.jgss.initiate {
com.sun.security.auth.module.Krb5LoginModule required principal="negotiatetestserver@SECURITYQA.COM"
useKeyTab=true keyTab=negotiatetestserver_keytab
storeKey=true debug=true;
};
com.sun.security.jgss.krb5.accept {
com.sun.security.auth.module.Krb5LoginModule required principal="negotiatetestserver@SECURITYQA.COM"
useKeyTab=true keyTab=negotiatetestserver_keytab
storeKey=true debug=true;
};com.ibm.security.jgss.initiate {
com.ibm.security.auth.module.Krb5LoginModule required principal="negotiatetestserver@SECURITYQA.COM"
useKeyTab=true keyTab=negotiatetestserver_keytab storeKey=true debug=true;
};
com.ibm.security.jgss.accept {
com.ibm.security.auth.module.Krb5LoginModule required principal="negotiatetestserver@SECURITYQA.COM"
useKeyTab=true keyTab=negotiatetestserver_keytab storeKey=true debug=true;
};This assumes you have transferred the keytab file “negotiatetestserver_keytab” generated in step 2 to your domain directory on Oracle WebLogic Server. If Oracle WebLogic Server is using Oracle JDK, specify following options in the Oracle WebLogic Server java command line:
-Dcom.ibm.security.jgss.debug=all -Djava.security.krb5.realm=SECURITYQA.COM -Djava.security.krb5.kdc=MACHINEC -Djava.security.auth.login.config= krb5Login.conf -Djavax.security.auth.useSubjectCredsOnly=falseWebLogic Server includes a security provider, the Negotiate Identity Assertion provider, to support single sign-on (SSO) with Microsoft clients. This identity assertion provider decodes Simple and Protected Negotiate (SPNEGO) tokens to obtain Kerberos tokens, validates the Kerberos tokens, and maps Kerberos tokens to WebLogic users. You need to configure a Negotiate Identity Assertion provider in your WebLogic security realm in order to enable SSO with Microsoft clients. See Configuring a Negotiate Identity Assertion Provider .
Install Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files(This step is applicable only if you plan to use AES256-SHA1 cipher strength. Skip this step for all other cipher strengths). You need to download and install this bundle which provides "unlimited strength" policy files which contain no restrictions on cryptographic strengths.
- For Oracle JDK 6: Download Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 6 here.
- For Oracle JDK 7: Download Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 7 here. Overwrite 2 jar files under “
/jre/lib/security” directory with 2 jar files inside downloaded zip file. - For IBM JDK 6 and above: Download Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy Files 7 here and follow installation instructions
In order for authentication to take place, the resource (JSP or Servlet) being accessed must be protected, and for the web application to participate in Single Sign On with the client.
Here’s the servlet code used in our case (SimpleTestServlet.java):
package wlstest.functional.security.negotiate.servlet;
import java.io.IOException;
import java.io.PrintWriter;
import java.util.Enumeration;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import javax.servlet.http.HttpUtils;
public class SimpleTestServlet extends HttpServlet
{
public void service(HttpServletRequest req, HttpServletResponse res)
throws ServletException, IOException
{
res.setContentType("text/html");
PrintWriter out = res.getWriter();
out.println("
");
out.println("
<title>Simple Test Servlet</title>
<script>(window.BOOMR_mq=window.BOOMR_mq||[]).push(["addVar",{"rua.upush":"false","rua.cpush":"false","rua.upre":"false","rua.cpre":"false","rua.uprl":"false","rua.cprl":"false","rua.cprf":"false","rua.trans":"SJ-e7979a39-7c9b-4b7c-bf2f-ac10ddd88d50","rua.cook":"true","rua.ims":"false","rua.ufprl":"false","rua.cfprl":"true","rua.isuxp":"false","rua.texp":"norulematch","rua.ceh":"false","rua.ueh":"false","rua.ieh.st":"0"}]);</script>
<script>!function(e){var n="https://s.go-mpulse.net/boomerang/";if("False"=="True")e.BOOMR_config=e.BOOMR_config||{},e.BOOMR_config.PageParams=e.BOOMR_config.PageParams||{},e.BOOMR_config.PageParams.pci=!0,n="https://s2.go-mpulse.net/boomerang/";if(window.BOOMR_API_key="DXNLE-YBWWY-AR74T-WMD99-77VRA",function(){function e(){if(!o){var e=document.createElement("script");e.id="boomr-scr-as",e.src=window.BOOMR.url,e.async=!0,i.parentNode.appendChild(e),o=!0}}function t(e){o=!0;var n,t,a,r,d=document,O=window;if(window.BOOMR.snippetMethod=e?"if":"i",t=function(e,n){var t=d.createElement("script");t.id=n||"boomr-if-as",t.src=window.BOOMR.url,BOOMR_lstart=(new Date).getTime(),e=e||d.body,e.appendChild(t)},!window.addEventListener&&window.attachEvent&&navigator.userAgent.match(/MSIE [67]\./))return window.BOOMR.snippetMethod="s",void t(i.parentNode,"boomr-async");a=document.createElement("IFRAME"),a.src="about:blank",a.title="",a.role="presentation",a.loading="eager",r=(a.frameElement||a).style,r.width=0,r.height=0,r.border=0,r.display="none",i.parentNode.appendChild(a);try{O=a.contentWindow,d=O.document.open()}catch(_){n=document.domain,a.src="javascript:var d=document.open();d.domain='"+n+"';void(0);",O=a.contentWindow,d=O.document.open()}if(n)d._boomrl=function(){this.domain=n,t()},d.write("<bo"+"dy onload='document._boomrl();'>");else if(O._boomrl=function(){t()},O.addEventListener)O.addEventListener("load",O._boomrl,!1);else if(O.attachEvent)O.attachEvent("onload",O._boomrl);d.close()}function a(e){window.BOOMR_onload=e&&e.timeStamp||(new Date).getTime()}if(!window.BOOMR||!window.BOOMR.version&&!window.BOOMR.snippetExecuted){window.BOOMR=window.BOOMR||{},window.BOOMR.snippetStart=(new Date).getTime(),window.BOOMR.snippetExecuted=!0,window.BOOMR.snippetVersion=12,window.BOOMR.url=n+"DXNLE-YBWWY-AR74T-WMD99-77VRA";var i=document.currentScript||document.getElementsByTagName("script")[0],o=!1,r=document.createElement("link");if(r.relList&&"function"==typeof r.relList.supports&&r.relList.supports("preload")&&"as"in r)window.BOOMR.snippetMethod="p",r.href=window.BOOMR.url,r.rel="preload",r.as="script",r.addEventListener("load",e),r.addEventListener("error",function(){t(!0)}),setTimeout(function(){if(!o)t(!0)},3e3),BOOMR_lstart=(new Date).getTime(),i.parentNode.appendChild(r);else t(!1);if(window.addEventListener)window.addEventListener("load",a,!1);else if(window.attachEvent)window.attachEvent("onload",a)}}(),"".length>0)if(e&&"performance"in e&&e.performance&&"function"==typeof e.performance.setResourceTimingBufferSize)e.performance.setResourceTimingBufferSize();!function(){if(BOOMR=e.BOOMR||{},BOOMR.plugins=BOOMR.plugins||{},!BOOMR.plugins.AK){var n="true"=="true"?1:0,t="cookiepresent",a="aohk2bqx3myxq2ablcuq-f-14ebef310-clientnsv4-s.akamaihd.net",i="false"=="true"?2:1,o={"ak.v":"39","ak.cp":"82485","ak.ai":parseInt("604074",10),"ak.ol":"0","ak.cr":8,"ak.ipv":4,"ak.proto":"h2","ak.rid":"3a4b13f9","ak.r":45919,"ak.a2":n,"ak.m":"dscx","ak.n":"essl","ak.bpcip":"3.142.173.0","ak.cport":35734,"ak.gh":"23.213.203.31","ak.quicv":"","ak.tlsv":"tls1.3","ak.0rtt":"","ak.0rtt.ed":"","ak.csrc":"-","ak.acc":"","ak.t":"1744918697","ak.ak":"hOBiQwZUYzCg5VSAfCLimQ==Xo5cciLQY4rrgB4KKT0ayY35Rl79kajSW0ogHgZErLZ9do7A5XYEuRJ1CaPn++Dqhm1G65Ewvx7GdUirwDzc6eHkf24aOuaGJDYVLoA43dxJ1FBsGey/lisdGiTa9qk5Uio8T+PKBwghRI5UQrTarBf41rpoRuXciepLng6m514Rn4WckTKFyiDxEtSyw1FT8m4fKg51MYErRpwZrDfSyuvJQ8KoRv8LLLVXF9NVpGDKRXDzZA1iTbp+Px/zlHmt/xQy/ETV8qL5qGu20S+eu5Pp9oW5/uwk32h1tYrNCxZXYUJK60YZmhrBgH1GBcGoQW20HduWrYzWj42S8LnZuDTnVyZ0uafnUFFwBO2FA+wij0K/lDbQM/mJa909R4GLYj/oIHDgtldexccbdb6RYvYVCJl0qzHnxLJ0A3NZ6fw=","ak.pv":"502","ak.dpoabenc":"","ak.tf":i};if(""!==t)o["ak.ruds"]=t;var r={i:!1,av:function(n){var t="http.initiator";if(n&&(!n[t]||"spa_hard"===n[t]))o["ak.feo"]=void 0!==e.aFeoApplied?1:0,BOOMR.addVar(o)},rv:function(){var e=["ak.bpcip","ak.cport","ak.cr","ak.csrc","ak.gh","ak.ipv","ak.m","ak.n","ak.ol","ak.proto","ak.quicv","ak.tlsv","ak.0rtt","ak.0rtt.ed","ak.r","ak.acc","ak.t","ak.tf"];BOOMR.removeVar(e)}};BOOMR.plugins.AK={akVars:o,akDNSPreFetchDomain:a,init:function(){if(!r.i){var e=BOOMR.subscribe;e("before_beacon",r.av,null,null),e("onbeacon",r.rv,null,null),r.i=!0}return this},is_complete:function(){return!0}}}}()}(window);</script>
");
out.println("
");
out.println("
<h3>Requested URL:</h3>
");
out.println("
<pre aria-label="Code block 5">");
out.println(HttpUtils.getRequestURL(req).toString());
out.println("</pre>");
Enumeration theEnum = getServletConfig().getInitParameterNames();
if (theEnum != null)
{
boolean first = true;
while (theEnum.hasMoreElements())
{
if (first)
{
out.println("
<h3>Init Parameters</h3>
");
out.println("
<pre aria-label="Code block 5">");
first = false;
}
String param = (String) theEnum.nextElement();
out.println(" "+param+": "+getInitParameter(param));
}
out.println("</pre>");
}
out.println("
<h3>Request information:</h3>
");
out.println("
<pre aria-label="Code block 5">");
print(out, "Request method", req.getMethod());
print(out, "Request URI", req.getRequestURI());
print(out, "Request protocol", req.getProtocol());
print(out, "Servlet path", req.getServletPath());
print(out, "Path info", req.getPathInfo());
print(out, "Path translated", req.getPathTranslated());
print(out, "Query string", req.getQueryString());
print(out, "Content length", req.getContentLength());
print(out, "Content type", req.getContentType());
print(out, "Server name", req.getServerName());
print(out, "Server port", req.getServerPort());
print(out, "Remote user", req.getRemoteUser());
print(out, "Remote address", req.getRemoteAddr());
print(out, "Remote host", req.getRemoteHost());
print(out, "Scheme", req.getScheme());
print(out, "Authorization scheme", req.getAuthType());
print(out, "Request scheme", req.getScheme());
out.println("</pre>");
Enumeration e = req.getHeaderNames();
if (e.hasMoreElements())
{
out.println("
<h3>Request headers:</h3>
");
out.println("
<pre aria-label="Code block 5">");
while (e.hasMoreElements())
{
String name = (String)e.nextElement();
out.println(" " + name + ": " + req.getHeader(name));
}
out.println("</pre>");
}
e = req.getParameterNames();
if (e.hasMoreElements())
{
out.println("
<h3>Servlet parameters (Single Value style):</h3>
");
out.println("
<pre aria-label="Code block 5">");
while (e.hasMoreElements())
{
String name = (String)e.nextElement();
out.println(" " + name + " = " + req.getParameter(name));
}
out.println("</pre>");
}
e = req.getParameterNames();
if (e.hasMoreElements())
{
out.println("
<h3>Servlet parameters (Multiple Value style):</h3>
");
out.println("
<pre aria-label="Code block 5">");
while (e.hasMoreElements())
{
String name = (String)e.nextElement();
String vals[] = (String []) req.getParameterValues(name);
if (vals != null)
{
out.print("<b> " + name + " = </b>");
out.println(vals[0]);
for (int i = 1; i<vals.length; i++)="" out.println("="" "="" +="" vals[i]);="" }="" out.println("<p="">");
}
out.println("</vals.length;></pre>");
}
out.println("
<h3>Request Attributes:</h3>
");
e = req.getAttributeNames();
if (e.hasMoreElements())
{
out.println("
<pre aria-label="Code block 5">");
while (e.hasMoreElements())
{
String name = (String)e.nextElement();
Object o = req.getAttribute(name);
if (o == null) continue;
out.println(" " + name + ": type=" + o.getClass().getName() + " str='" + o.toString() + "'");
}
out.println("</pre>");
}
out.println("
");
}
private void print (PrintWriter out, String name, String value)
{
out.print(" " + name + ": ");
out.println(value == null ? "<none>" : value);
}
private void print (PrintWriter out, String name, int value)
{
out.print(" " + name + ": ");
if (value == -1)
out.println("<none>");
else
out.println(value);
}
}<web-app>
<display-name>Simple Test Servlet (Basic Auth)</display-name>
<security-constraint>
<web-resource-collection>
<web-resource-name>BasicAuthSimpleTestServlet</web-resource-name>
<url-pattern>/*</url-pattern>
<url-pattern>/</url-pattern>
<http-method>POST</http-method>
<http-method>GET</http-method>
</web-resource-collection>
<auth-constraint>
<role-name>negotiateAdminRole</role-name>
</auth-constraint>
<user-data-constraint>
<description>no description</description>
<transport-guarantee>NONE</transport-guarantee>
</user-data-constraint>
</security-constraint>
<security-role>
<role-name>negotiateAdminRole</role-name>
</security-role>
<login-config>
<auth-method>BASIC</auth-method>
<realm-name>default</realm-name>
</login-config>
<servlet>
<servlet-name>BasicAuthSimpleTestServlet</servlet-name>
<servlet-class>wlstest.functional.security.negotiate.servlet.SimpleTestServlet</servlet-class>
</servlet>
<welcome-file-list>
<welcome-file>/BasicAuthSimpleTestServlet</welcome-file>
</welcome-file-list>
<servlet-mapping>
<servlet-name>BasicAuthSimpleTestServlet</servlet-name>
<url-pattern>/</url-pattern>
</servlet-mapping>
</web-app><weblogic-web-app>
<security-role-assignment>
<role-name>negotiateAdminRole</role-name>
<principal-name>negotiateAdmin</principal-name>
<principal-name>Administrators</principal-name>
</security-role-assignment>
</weblogic-web-app>Client Configuration
For Single Sign On to occur you will need an authenticated Microsoft client, belonging to the domain controlled by your realm, and requesting access to the Oracle WebLogic Server service
Configuring Internet Explorer BrowserTo configure an Internet Explorer browser to use Windows authentication, follow these procedures in Internet Explorer.
Configure Local Intranet Domains- In Internet Explorer, select Tools > Internet Options.
- Select the Security tab.

Figure 3: Local Intranet Dialog Box for Internet Explorer
- Select Local intranet and click Sites.
- In the Local intranet popup, ensure that the Include all sites that bypass the proxy server and Include all local (intranet) sites not listed in other zones options are checked.
- Click Advanced.
- In the Local intranet (Advanced) dialog box, add all relative domain names that will be used for Oracle WebLogic Server instances participating in the SSO configuration (for example, myhost.example.com) and click OK.

Figure 5: Configure Intranet Authentication
- Select Tools > Internet Options.
- Select the Security tab.
- Select Local intranet and click Custom Level... .
- In the Security Settings dialog box, scroll to the User Authentication section.
- Select Automatic logon only in Intranet zone. This option prevents users from having to re-enter logon credentials, which is a key piece to this solution.
- Click OK.
If you have a proxy server enabled:
- Select Tools > Internet Options.
- Select the Connections tab and click LAN Settings.
- Verify that the proxy server address and port number are correct.
- Click Advanced.
- In the Proxy Settings dialog box, ensure that all desired domain names are entered in the Exceptions field.
- Click OK to close the Proxy Settings dialog box.
Configuring Mozilla Firefox Browser
To configure a Firefox browser to use Windows Integrated authentication, complete the following steps:
- Start Firefox.
- Enter about:config in the Location Bar.
- Enter the filter string network.negotiate.
- Set the preferences as shown in Figure below:

Figure 6: Preferences Required in Firefox for Windows Integrated Authentication
Configuring Google Chrome Browser
No special configuration needed for Chrome Browser.
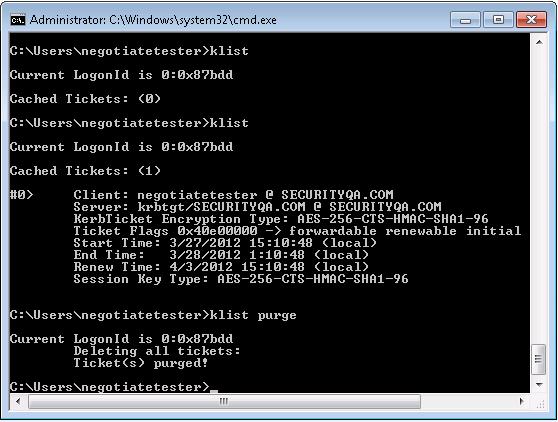
Figure 7: Using klist to view and purge tickets
- Login to MachineA (Browser Client) as user “SECURITYQA.COM\
- Open command prompt and run 'klist purge'. This is to purge any existing tickets.
- Open browser and access url of the web application. In this case, we are accessing a servlet which provides basic HTTP header information:

Figure 8: Servlet displaying HTTP info after SPNEGO authentication
- If the SSO was unsuccessful you will be prompted for username/password by the browser. In this case you need to check wls server logs for exception (Check Troubleshooting section below).

Figure 9: Browser prompting for username/password after SPNEGO failure
- Confirm if browser is sending SPNEGO tokens. Look for message “"Authorization: Negotiate YII…”. This means SPNEGO token is being passed by browser to Oracle WebLogic Server.
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:7.0.1) Gecko/20100101 Firefox/7.0.1
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Connection: keep-alive
Authorization: Negotiate YIIGzQYGKwYBBQUCoIIGwTCCBr2gMDAuBgkqhkiC9xIBAgIGCSqGSIb3EgECAgYKKwYBBAGCNwICHgYKKwYBBAGCNwICCqKCB
ocEggaDYIIGfwYJKoZIhvcSAQICAQBuggZuMIIGaqADAgEFoQMCAQ6iBwMFACAAAACjggUCYYIE/jCCBPqgAwIBBaEQGw5TRUNVUklUWVFBLkNPTaIrMCmgAwIBA
qEiMCAbBEhUVFAbGGFkYzIxNzA3MTkudXMub3JhY2xlLmNvbaOCBLIwggSuoAMCARGhAwIBJKKCBKAEggSc8v4RphGvP7CinPf4mhiBzyfZWQG …- You can also check if Oracle WebLogic Server is using correct cipher in the Oracle WebLogic Server log.
For Oracle JDK:
>>>Pre-Authentication Data:
PA-DATA type = 19
PA-ETYPE-INFO2 etype = 17
>>>Pre-Authentication Data:
PA-DATA type = 2
PA-ENC-TIMESTAMP
>>>Pre-Authentication Data:
PA-DATA type = 16
>>>Pre-Authentication Data:
PA-DATA type = 15
AcquireTGT: PREAUTH FAILED/REQUIRED, re-send AS-REQ
Updated salt from pre-auth = SECURITYQA.COMnegotiatetestserver
>>>KrbAsReq salt is SECURITYQA.COMnegotiatetestserver
Pre-Authenticaton: find key for etype = 17
AS-REQ: Add PA_ENC_TIMESTAMP now
>>> EType: sun.security.krb5.internal.crypto.Aes128CtsHmacSha1EType
>>> KrbAsReq calling createMessage
>>> KrbAsReq in createMessage
>>> KrbKdcReq send: kdc=rno05089 UDP:88, timeout=30000, number of retries =3, #bytes=241
>>> KDCCommunication: kdc=rno05089 UDP:88, timeout=30000,Attempt =1, #bytes=241
>>> KrbKdcReq send: #bytes read=100
>>> KrbKdcReq send: #bytes read=100
>>> KdcAccessibility: remove rno05089
>>> KDCRep: init() encoding tag is 126 req type is 11JGSS_DBG_PROV] getMechs: Mechanism(s) supported by provider IBMJGSSProvider
[JGSS_DBG_PROV] 1.3.6.1.5.5.2
[JGSS_DBG_PROV] getMechs: Mechanism(s) supported by provider IBMJGSSProvider
[JGSS_DBG_PROV] 1.2.840.113554.1.2.2
[JGSS_DBG_PROV] getMechs: Mechanism(s) supported by provider IBMSPNEGO
[JGSS_DBG_PROV] 1.3.6.1.5.5.2
[JGSS_DBG_PROV] getMechs: 2 unique mechanism(s) found
[JGSS_DBG_PROV] [0]: 1.3.6.1.5.5.2
[JGSS_DBG_PROV] [1]: 1.2.840.113554.1.2.2
[JGSS_DBG_CTX] Default list of negotiable mechs:
1.2.840.113554.1.2.2
[JGSS_DBG_CTX] AuthenticatorCache, scope of bucket122
[JGSS_DBG_CTX] ticket enc type = rc4-hmac
[JGSS_DBG_CTX] Successfully decrypted ticket
[JGSS_DBG_CTX] Put authz info in cache
[JGSS_DBG_CTX] Session key type = rc4-hmac
[JGSS_DBG_CTX] Successfully decrypted authenticator
[JGSS_DBG_CTX] Remote subkey type = rc4-hmac
[JGSS_DBG_CTX] No delegated creds from peer
[JGSS_DBG_CTX] Received channel binding checksumTroubleshooting
Here are typical exceptions you might encounter during SPNEGO setup along with solutions:
- kinit: Cannot contact any KDC for requested realm while getting initial credentials. Your computer successfully sent out a request, but the KDC never responded. The network is probably down between your host and the KDC, or you are behind a firewall.
- javax.security.auth.login.LoginException: KrbException:: Pre-authentication information was invalid (24) - Preauthentication failed. The principal exists in kerberos but the password is wrong. This is a password problem. Double check the validity of your keytab, or of the password that you have entered.
- Exception: krb_error 0 Cannot retrieve key from keytab for principal xxx No error. The keytab file you have provided was not created for that principal, or there is no such file (this will be easy to check) . If the file does exist, the principal xxx might exist in the AD server, but this keytab is not for it. On the other hand, principal might not exist at all.
- javax.security.auth.login.LoginException: KrbException: KDC has no support for encryption type (14) - KDC has no support for encryption type. Your KDC does not support the encryption type requested. Please choose an encryption type that is supported by the KDC you are using.
- <Debug> <SecurityDebug> <000000> <Found NTLM token when expecting SPNEGO>. This is a very common error. It means that the Oracle WebLogic Server was ready to extract a SPNEGO token but could not find one in the request sent by the browser. The browser is not set up correctly to send a spnego token, go back to the client configuration, and double check the browser configuration. Something is wrong in your SPN definition: Either no SPN was defined for this service, or you have duplicate SPNs, which means that the SPN resolved in more than one principal associated with it.
- Exception: weblogic.security.providers.utils.NegotiateTokenException: GSSException: No valid credentials provided (Mechanism level: Attempt to obtain new ACCEPT credentials failed!). This is very common exception that covers anything that might have gone wrong during the process of the Oracle WebLogic Server loading the JAAS configuration from the krb5Login.conf file to reading the keytab and successfully decoding the SPNEGO ticket. The krb5Login.conf file could not be found or opened - double-check the way you have specified it to Oracle WebLogic Server, double check existence and permissions. There could be some wrong syntax inside the krb5Login.conf
- java.lang.SecurityException at javax.security.auth.login.Configuration.getConfiguration. There was a problem processing the JAAS login configuration file, possibly due to a syntax error in the file. Check the configuration file carefully for errors.
- GSSException: No valid credentials provided (Mechanism level: Attempt to obtain new INITIATE credentials failed! (null)) . . . Caused by: javax.security.auth.login.LoginException: Clock skew too great. Kerberos requires the time on the KDC and on the client to be loosely synchronized. (The default is within 5 minutes.) If that's not the case, you will get this error. Synchronize the clocks (or have a system administrator do so).
Conclusion
SSO Cross-platform authentication is achieved by emulating the negotiate behavior of native Windows-to-Windows authentication services that use the Kerberos protocol. In order for cross-platform authentication to work, Oracle WebLogic Server can be used to parse SPNEGO tokens in order to extract Kerberos tokens which are then used for authentication thus providing transparent authentication to the end user.

