Permissioned blockchain
Introduction
What is a blockchain?
In broad terms, a blockchain is an immutable transaction ledger, maintained within a distributed peer-to-peer (p2p) network of nodes. In essence, blockchains serve as a decentralized way to store information.
Each of these distributed nodes maintains a copy of the ledger by aggregating transactional blocks that have been verified by a consensus protocol and signed with a hash (or cryptographic signature) that binds that block to a preceding one. This way, the network maintains an unbroken chain of events.
Key properties of blockchains
- Shared and transparent data access
- Immutable/tamper-evident ledgers
- Validated /non-repudiable transactions
- Confidential records and transactions
Types of blockchains
Blockchain applications can be used for a variety of operations such as finance, supply chain monitoring, and identity validation. Depending on the application and the need of participating entities (security, performance, etc.) there are two types of blockchains available, permissioned and permissionless. We’ll take a brief tour of both below and then explore permissioned blockchains in greater detail below.
Permissioned blockchains - Closed networks with limited decentralization, an additional access control layer, and designated entities.
Permissionless blockchains - Open, decentralized networks with universal consensus validation; anyone can join the network and possess a copy of the ledger.
Permissionless and permissioned blockchains compared (overview)
| Permissioned | Permissionless | |
|---|---|---|
| Alternate designations | Private, permissioned sandbox | Public, trustless |
| Examples | Ripple | Bitcoin, Ethereum |
| Key attributes |
|
|
| Benefits |
|
|
| Drawbacks |
|
|
| Use cases |
|
|
Permissioned blockchains
Now, let’s take a closer look at permissioned blockchains. Permissioned blockchains are blockchains that are closed (i.e., not publicly accessible) or have an access control layer. This additional layer of security means that the blockchain can only be accessed by users with permissions. Permissioned users are only able to perform blockchain operations within the strict confines of roles assigned to them by the ledger administrators and require that they authenticate themselves through certificates or digital identifier methods. In addition, the roles would dictate what information a user would be able to access.
Aspects of a permissioned blockchain
Decisions are authorized by a private group
Decisions are made by the owners of the network through a central, pre-defined level.
Security
Permissioned blockchains provide the operating organization granular control over permissions, data access, and the scope of user roles.
Decentralization isn’t fixed
Permissioned blockchains can either be fully centralized or partially decentralized. Its members typically decide on the network’s level of decentralization and the mechanisms for consensus.
Transparency is not required
Unlike permissionless blockchains, permissioned blockchains do not need to be transparent. Transparency is
optional, as most permissioned blockchain networks are specifically intended to not be transparent for
security purposes. Levels of transparency usually depend on the goals of the organization running the
blockchain network.
In the meantime, the ledger maintains a record of every transaction and the identities of the participating
parties.
Lack of anonymity
Access to the identify of every transactional participant can be crucial information for private entities concerned with accountability and a provable chain of custody. Every change is tracked to a specific user, so network administrators can have instantaneous access to has made a change to the system and when.
Consensus mechanisms
Because of the structure of permissioned blockchains, they don’t use the same types of consensus protocols as permissionless ones. Most commonly, organizations that deploy permissioned blockchains use one (or more) of the following three protocols: Practical Byzantine Fault Tolerance (PBFT), federated, or round-robin consensus.
PBFT – PBFT is an improved version of the original BFT protocol where all voting nodes much reach a consensus, but one or more parties are considered unreliable. In this model, a network’s safety and stability are guaranteed so long as the required minimum percentage of nodes are behaving honestly and properly.
Federated (or Federated Byzantine Consensus) - In a federated consensus, there’s a set of transaction validators trusted by each node in the blockchain that receives and sorts the transactions. Once a minimum number of these validators agree, a consensus is reached.
Round-robin - In a round-robin consensus, nodes are selected pseudo-randomly to create blocks. Once chosen, a node must pass through a cooling-off period before it can reenter the pool and be available again for consensus participation.
Advantages of permissioned blockchain
One of the most significant advantages of permissioned blockchains is the high level of privacy and security they can provide. Without a verified set of credentials and access, no user can access or alter transaction information without permission.
Another advantage is flexibility when it comes to decentralization. It can be incremental or fully centralized, giving businesses more freedom to participate without having to worry about the risks associated with a highly centralized network.
Permissioned blockchains are also highly customizable and can accommodate configurations and integrations based on an organization’s needs. And with knowledge of every user and their actions on the network, a verifiable chain of custody can be established for every transaction.
Lastly, these types of blockchains are both scalable and highly performant due to the limited number of nodes needed to manage transaction verifications.
Disadvantages of permissioned blockchain
While lack of transparency can be a potential point of concern for permissioned blockchains, the issue is usually mitigated by the implicit trust placed in the governing authority. In a business context, consensus mechanisms and the smart contracts that moderate transactions on the network are agreed upon by the participating parties and maintained in secure, isolated containers. With this additional layer of computational security and measure of implicit trust, a properly provisioned permissioned blockchain can offset the security risk posed by bad actors.
Why permissioned blockchains are ideal for business applications
Many enterprise use cases require performance characteristics that permissionless blockchain technologies are presently unable to deliver because of limitations due to inefficiency and scalability. Additionally, in instances where permissioned blockchains are replacing existing secure, centralized networks, the identity of the participants is an essential requirement, such as in the case of financial transactions where Know-Your-Customer (KYC), Anti-Money Laundering (AML), and supply-chain provenance regulations must be followed.
In general, then, for a blockchain network to be ready for enterprise use, it should possess the following requirements:
- Participants must be identified/identifiable
- Networks need to be permissioned
- High transaction throughput performance
- Low latency of transaction confirmation
- Privacy and confidentiality of transactions and data pertaining to business transactions
Business value
Let’s quickly review and see how permissioned blockchains stack up against these requirements. In terms of added value, permissioned blockchains:
- Increase business velocity by accelerating transactions, enabling new business models and revenue streams
- Automate multi-party business processes
- Reduce the cost and risk of using intermediaries
- Reduce the cost of fraud and regulatory compliance
- Improve data quality and timeliness by avoiding offline reconciliation and manual exception handling
- Increase auditability and trust; reduce audit costs
Comparing the two, permissioned blockchains are well positioned to achieve all the stated business requirements.
Use case examples
So, how are permissioned blockchains being used by businesses? While still an emerging business model, they have already found a wide variety of applications. Permissioned blockchains have been used to manage supply chains, create contracts, handle claims, verify payment between parties, and administer user identity.
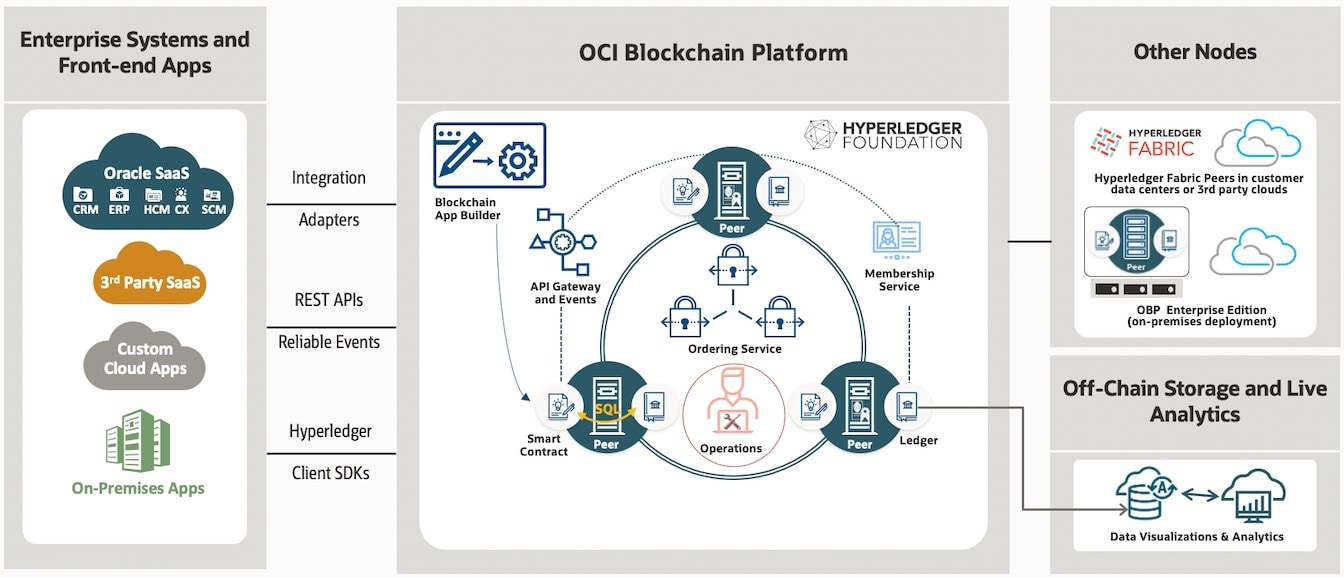
Oracle Blockchain Platform (OBP) – extending the paradigm
Now that we’ve explored permissioned blockchains and the ways in which they can be ideal for business, let’s take a quick look at how Oracle is adding value to the blockchain platform. The Oracle Cloud Infrastructure Blockchain Platform is a tokenless managed blockchain service for running smart contracts and maintaining a tamper-proof distributed ledger. Built on the open source Hyperledger Fabric, it simplifies the development of secure and verifiable applications that share immutable, trusted data with third parties such as suppliers and financial institutions. OBP goes further by extending Hyperledger Fabric with several enhancements for greater resilience, performance, scalability, security, manageability, and enterprise integration.
As a preassembled Platform as a Service (PaaS), OBP includes all the dependencies required to support a blockchain network: compute, storage, containers, identity services, event services, and management services. OBP is deeply integrated with foundational services in Oracle Cloud and provides additional capabilities (e.g., REST proxy for synchronous transactions and an operations console with several configuration, administration, and monitoring capabilities) while maintaining compatibility with Hyperledger Fabric at the protocol and API level.
Additionally, OBP includes the blockchain network console to support integrated operations. This helps you start developing applications within minutes and enables you to complete a proof of concept in days or weeks rather than months.
OBP has had proven successes in a wide variety of settings, including:
- banking and financial services
- retail
- manufacturing and logistics
- food, agriculture, and Consumer Packaged Goods (CPG)
- transportation and logistics
- healthcare and life sciences
How to get started with OBP
If you’d like to learn more about OBP and begin your development journey, check out some of the following resources:
Glossary of terms
- Consensus protocol
A consensus mechanism is the way in which blockchains come into agreement about how transactions are processed and immutably stored on the platform.
Since blockchains are dynamic and constantly changing states, the shared ledger technologies that they rely upon require an efficient, reliable, and secure mechanism to ensure that all the transactions occurring on the network are genuine and that all participants agree on the state of the ledger. This way, ledgers are protected against potential threats or anomalous states by reaching a mutual agreement about how the ledger should look.
At its core, the consensus mechanism is a fault-tolerant set of rules that decides on the legitimacy of contributions made by the various participants of the blockchain.
- Distributed ledger
A distributed ledger is a database that is synchronously shared across different nodes in a network. It helps retain a record of transactions or contracts that have been created by participants in the system.
Participating nodes are expected to be able to access the shared ledger and possess an identical copy of it. Any changes or additions made to the ledger are reflected and copied to all participants.
- Smart contract
Smart contracts are essentially self-executing pieces of business logic that mediate a specific transaction on the blockchain.
Contained within the code of the transaction is details of the agreement between each of the participants. This code autonomously controls the execution of the smart contract and ensures transactions are trackable and irreversible.