What's new–Cloud Guard Instance Security
Cloud Guard Instance Security
With Instance Security, Cloud Guard is expanding from security posture management to cloud workload protection, ensuring you can meet your security needs in one place with consistent visibility, near real-time protection, and a holistic understanding of your cloud security posture.
Instance Security collects and aggregates important security information about compute instances, such as security alerts, vulnerabilities, and open ports, to provide actionable guidance for detection and prevention. Customers need the ability to detect suspicious processes, open port creation, and script execution for their workloads, which requires operating system–level visibility. Instance Security provides new Oracle-managed, out-of-the box detections and customer-managed queries that can be used for threat hunting.
To get the value of Cloud Guard Instance Security in your tenancy, enable Cloud Guard and apply an Instance Security detector recipe to your in-scope compute instances.
For additional information about Cloud Guard Instance Security or how to enable it, please review the service documentation. For information on pricing, please review the pricing documentation.
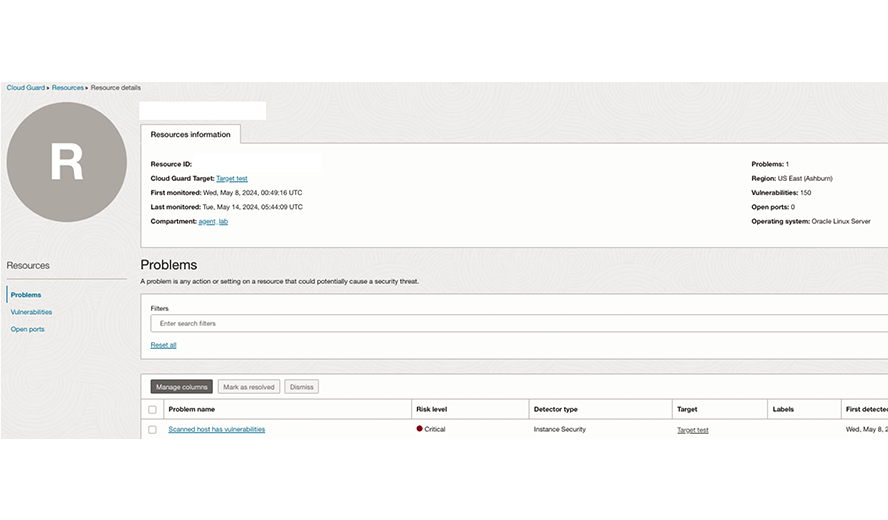
Unified view of security problems
See all security problems in one place with Oracle Cloud Guard
Instance Security is part of Cloud Guard. Cloud Guard’s resource view allows you to see all security problems associated with a compute instance in one place. This provides a bird’s-eye view of security problems detected using Cloud Guard, such as operating system–level vulnerabilities and open ports for individual instances.
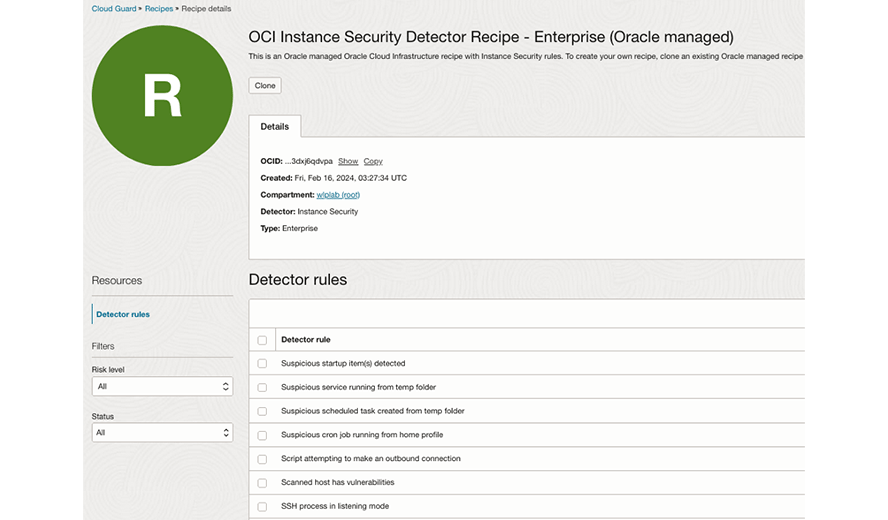
Out-of-the-box detector rules
New MITRE-aligned, out-of-the-box detector rules
Cloud Guard Instance Security detector recipes monitor your compute hosts for suspicious activity. Oracle-managed, MITRE-aligned, out-of-the-box detections reduce manual effort for security analysts to help identify high-risk activities.
Instance Security customers can collect data for the purpose of detecting security anomalies and get deep insights into their operating systems, without requiring any kernel code modifications.
The detector catalog is continuously expanding to align with our customers’ needs.
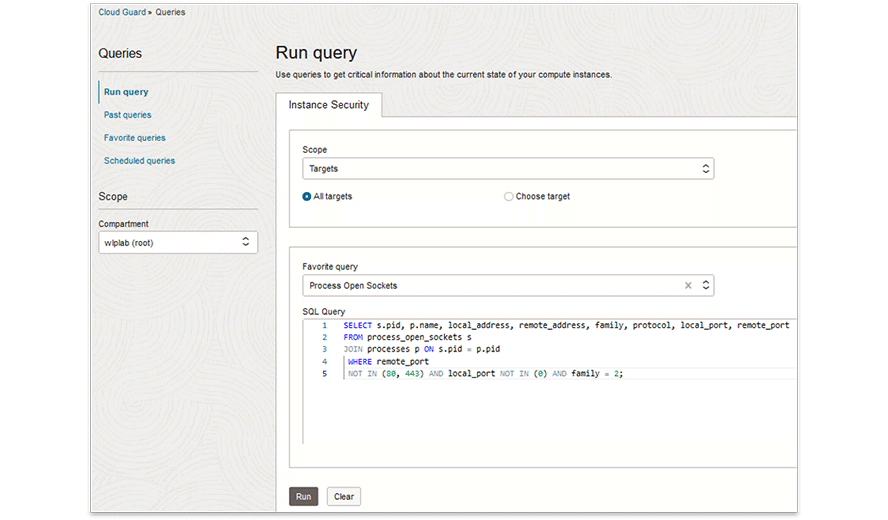
Live queries
Run live queries on your hosts for detections and threat hunting
Your security operations team can run queries on compute instances on an ad hoc basis. This provides visibility into the state of the fleet.
Instance Security runs osquery (osquery 5.5.1) under the hood, which leverages a relational data model to describe an instance. Osquery is a performant, open source, multiplatform software that helps you gain visibility and insights into your fleet. It can collect and normalize data independently of the operating system, increasing visibility across your infrastructure.
Osquery has hundreds of out-of-the-box tables that provide information about an instance, ranging from running processes to loaded kernel extensions. Instance Security supports a majority of the open source osquery tables in addition to custom-built Oracle Cloud Infrastructure (OCI) tables.
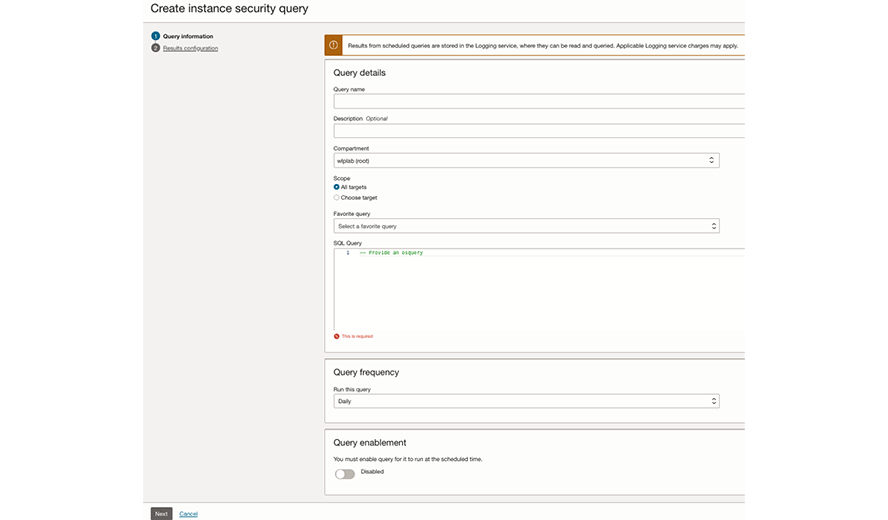
Scheduled queries
Schedule queries on your hosts for your compliance and audit needs
After you’ve run a query and are happy with the result, you can schedule the query to run periodically.
If you have compliance requirements that require you to inspect your instances and provide evidence of the security controls in place, you can use scheduled queries. Instance Security integrates with the Oracle Cloud Infrastructure Logging service, and you can configure it to send your raw data to a SIEM or third-party data aggregator from OCI Logging.