Access Governance Features
What’s New?
Oracle Access Governance is continually evolving to enhance identity governance and administration across cloud and on-premises environments. Here’s an overview of the new features we’ve added recently to improve your Oracle Access Governance experience. These advancements underscore our commitment to providing robust and intelligent access governance solutions that help you maintain security and compliance across diverse IT environments.
For additional information about Oracle Access Governance, please review the service documentation. For information on pricing, please review the pricing documentation.
New features
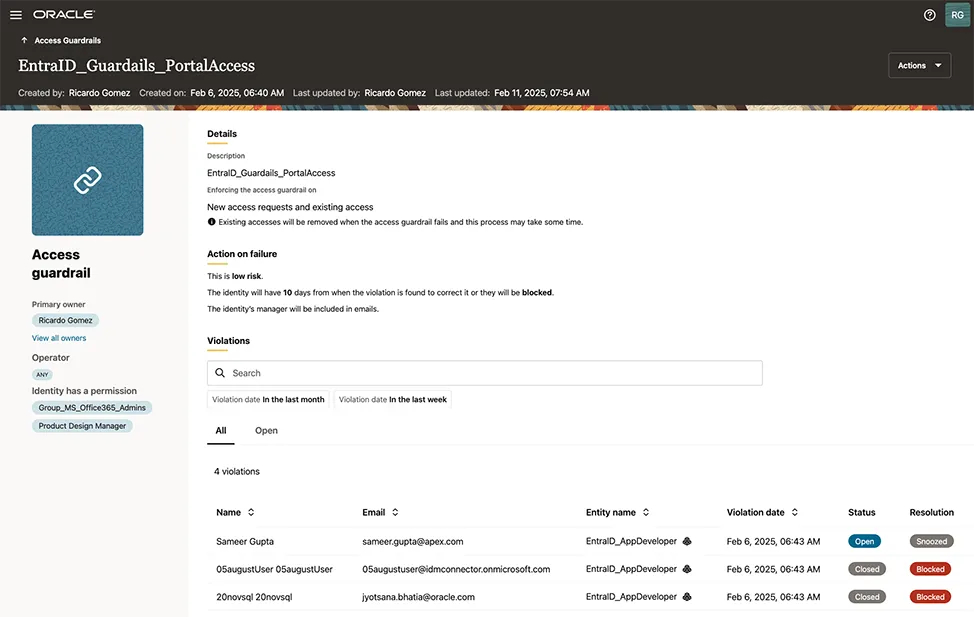
Access guardrails: Strengthening segregation of duties (SoD) with metadata-driven rules
To help facilitate compliance and mitigate risks, Oracle Access Governance has introduced access guardrails. This feature enforces segregation of duties (SoD) by implementing metadata-driven rules to define eligibility criteria for granting access bundle permissions. Examples include training requirements, toxic combinations of permissions, and identity attributes such as organization and location. Administrators can define and manage these rules to automatically detect and remediate potential SoD violations, thereby maintaining a secure and compliant access framework.
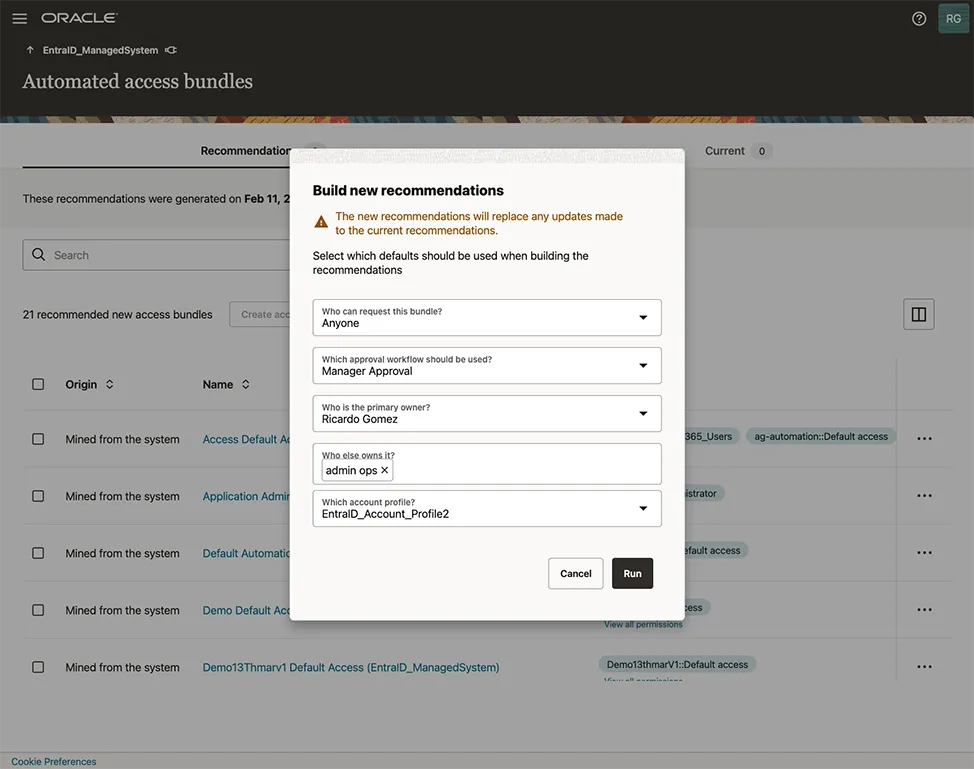
AI Agents: Automating Access Bundles with AI-powered Mining and Generative AI
Leveraging AI, Oracle Access Governance now includes embedded AI agents that streamline application onboarding. These AI agents mine existing permissions and automatically generate access bundle recommendations for managed applications, complete with Generative AI-generated naming conventions. Additionally, the prescriptive analytics-powered AI agent provides insights into outlier access patterns, enabling swift remediation actions to uphold security standards.
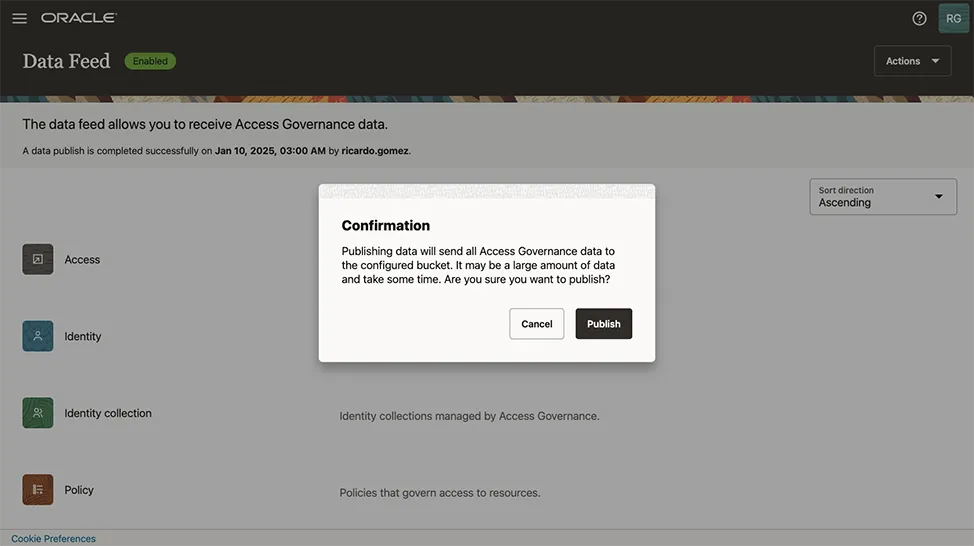
Enhanced Event Data Publisher: Integrating with OCI for Advanced Monitoring
The Event Data Publisher has been enhanced to export audit histories into Oracle Cloud Infrastructure (OCI) Buckets or OCI Streams. This enhancement allows for the inclusion of Access Governance operational data, enabling customers to monitor their Access Governance operations and audit data effectively. With Oracle’s reference implementation, this data can be seamlessly integrated into Business Intelligence (BI) dashboards for comprehensive analysis.
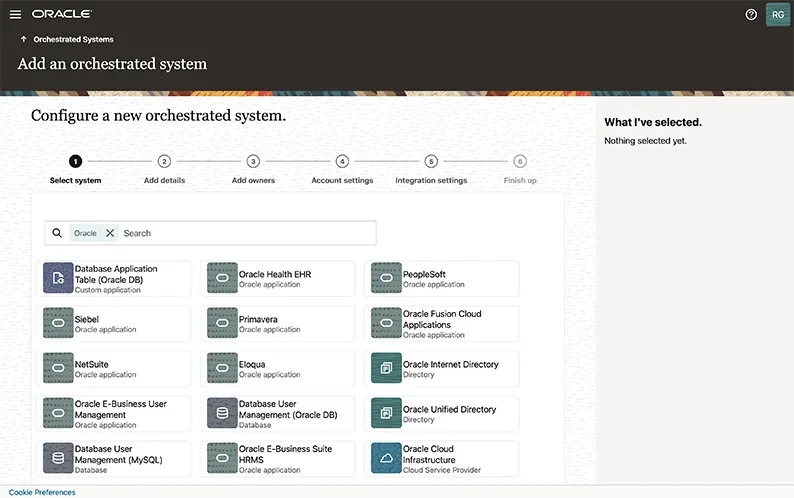
Deep Integration with Oracle Ecosystem: Automating identity lifecycle across the ecosystem
Oracle Access Governance offers automated user provisioning, access controls, audit capabilities, and compliance reporting across the entire digital ecosystem. When integrated natively with Oracle Cloud Applications, it ensures that the right individuals have access to the appropriate resources at the right times. This integration maximizes operational efficiency through easy integrations with non-Oracle business technologies.
Simplified Audit Reporting: Streamlining audit reporting process with ease
Audit processes are now more straightforward with Oracle Access Governance's support for compliance reports. The platform provides easy access to who have access to what audit logs, which can be readily downloaded to facilitate compliance reporting and auditing procedures such as SOC1, SOC2, and ISO27001.
Identity orchestration
Access Governance seamlessly integrates with business-critical systems—including Oracle Cloud Infrastructure and industry-leading Oracle applications, such as Oracle Fusion Cloud Applications, Oracle Health EHR, Oracle E-Business Suite, PeopleSoft, and more. The identity orchestration feature accelerates onboarding by seamlessly integrating with cloud and on-premises systems for fast, cordless application setup. It extracts, correlates, and transforms data across multiple sources, providing a unified view of user access.
Lifecycle management
Access Governance simplifies identity lifecycle management across diverse environments by centralizing user access control. It empowers users with self-service capabilities, enabling them to manage identity details, request access, delegate tasks, and review permissions. With automated identity lifecycle management, the system supports secure onboarding, transfers, and offboarding, covering joiner, mover, and leaver scenarios. Additionally, it synchronizes and reconciles accounts across systems, allowing for accurate access assignments and reducing manual workloads.
Access control
Access Governance offers a comprehensive access control framework to help you manage on-premises and cloud permissions with precision and automation. It supports multiple permission models, including role-based access control for assigning permissions based on job roles such as finance analyst or HR manager, attribute-based access control for access tied to identity attributes such as location or job code, and policy-based access control for defining access policies, such as a policy that allows a healthcare provider to access patient records within their area of specialty. This flexible, automated approach gives you granular, customizable control over access across diverse environments.
Access certification
Access certification helps prevent excessive or unauthorized access by allowing you to use certification campaigns to monitor and validate user permissions. Certification campaigns assign review tasks to relevant users, such as managers or entitlement owners, to periodically evaluate access or trigger reviews based on events such as role or location changes. Reviewers can approve or revoke access, and all decisions are recorded to support regulatory compliance, ensuring that access aligns with organizational security policies and compliance requirements.
Process automation
Easily create lightweight no-code workflows for access control and governance. Visualize and design linear or parallel workflows and seamlessly integrate user management, management chains, and identity collection into the workflow process.
Automate access control with AI-assisted capabilities, including access bundle onboarding, provisioning, and access reviews. By leveraging peer group analysis, outlier detection, and risk evaluation, Access Governance provides actionable insights and prescriptive recommendations to improve risk awareness and reduce manual efforts.
Compliance
Access Governance helps you maintain governance and compliance by providing a centralized view of all identity and access data in addition to tools for managing access policies, conducting risk assessments, and auditing compliance. It provides out-of-the-box reports with graphical insights and audits for various compliance activities related to HIPAA, GDPR, SOX, and more. Access Governance provides instant auditability of access trends and entitlement risk so you can avoid costly and time-consuming manual access reviews.